Cloud Security

Cloud security defense in depth is a comprehensive
strategy designed to protect cloud environments
through multiple layers of security controls. As
businesses increasingly adopt cloud computing to
harness its advantages, they face an ever-expanding
array of cyber threats. Adopting a defense in depth
approach addresses these challenges by integrating
a range of security measures, including network security, automation, visibility, endpoint protection, threat intelligence, and more.
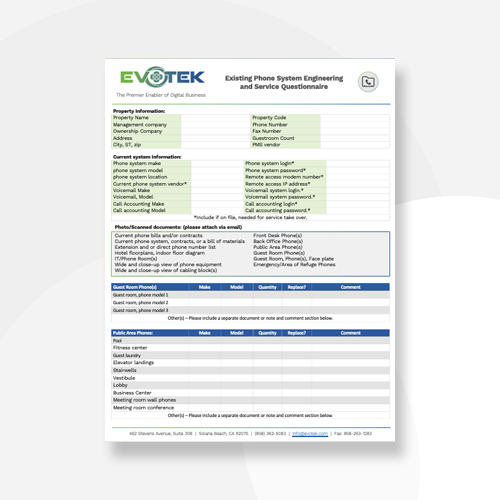
Phone System Questionnaire
Cloud Security

Cloud Security has been a critical area of focus for IT, product, and cybersecurity teams for multiple years now. It has also been an area that continually gets more complicated, and as a byproduct, misunderstood. The reasons for this are many, but among the chief of these reasons are evolving cloud platforms, additional security capabilities introduced by new and developing vendor solutions, and shifting business and threat landscapes that change at inconsistent rates and with differing levels of volatility.
Administrative Governance Maturity Assessment

Make purposeful decisions to improve business efficiency, reduce organizational risk, and establish innovative frameworks
Detecting Artificial Intelligence

The urgency to recognize the origin of digital content is spawning many detection solutions. As generative artificial intelligence detectors overcome current limitations, they will attempt to keep pace with sophisticated generative model development.
Wireless Site Survey

The EVOTEK Wireless Site Survey assesses the unique Wireless technology and architecture the client has deployed to support a high-performing, secure, and scalable wireless network. This assessment will identify any problems that exist within the wireless coverage area and the capacity of a client’s wireless support within their building(s). After the assessment, a client will receive a report detailing the current coverage area, client capacity, and the recommendations required to support their employee and customers’ wireless needs.
Firewall Assessment

The EVOTEK Firewall Assessment serves to assess the unique set of network technologies and architecture required to support a secure, high-performing, and reliable network. This assessment will identify any problems and opportunities that exist within a firewall’s configuration or architecture. After the assessment,
a client will receive a report detailing any changes required to support their information security and business needs.
Cloud Enablement

The EVOTEK Cloud Enablement service helps your organization accelerate cloud adoption. This service helps you tackle challenges around shared responsibilities and determine which groups are accountable for different parts of your cloud infrastructure. It also assists with securing your cloud infrastructure and facilitating the proper governance to manage and grow your cloud environment, while helping you plan for cloud a solid migration strategy for the future.
Email Security Gateway Health Check

An Email Security Gateway Health Check and Assessment aims to tune the organization’s email gateway and ensure its ongoing efficacy, configuration, and alignment with current email-borne threats. The scope of this assessment serves to identify vulnerabilities, mitigate email-based threats, protect sensitive information, ensure regulatory compliance, safeguard the organization’s reputation, and drive continuous improvement in email security. Email can be the easiest entry point for bad actors and outside threats, if not properly monitored.
Data Governance

The EVOTEK Data Governance Program enables organizations to assess and manage data threats and vulnerabilities in the current landscape. It helps establish data classification goals and maturity within the organization while working closely with the client’s staff to define objectives and strategies. Our team of experienced BISO and CISO advisors utilize insights from the discovery process to provide a comprehensive program with actionable recommendations for improving data governance. The program enables organizations to enhance data management, mitigate risks, and secure their data assets.
